For running applications sandboxed in Linux, Firetools is a good utility to do so. Sandboxing is essentially restricting applications in their own space and thereby limiting their reach to the overall system. This is a security layer to prevent any malicious programs to have full access to the system.
Firetools is a graphical front-end for the command-line sandboxing tool Firejail.
Installing Firetools:
To use Firetools in Linux Mint, first install it from the Terminal by typing in:
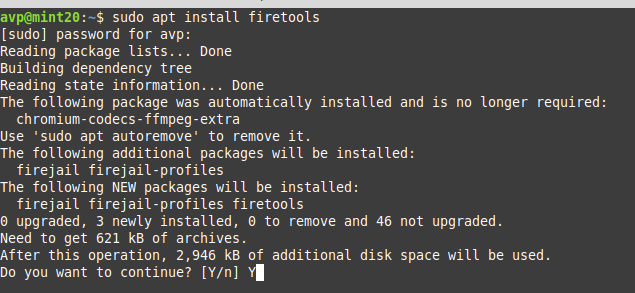
Once installed, it will show up in the System menu.
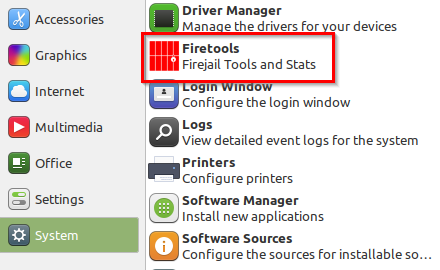
Using Firetools:
Launch Firetools to begin. This will show a menu which is the Sandbox Launcher.

A jail icon will also be visible in the system tray indicating that Firetools is now running.
![]()
By default, most of the applications that are installed will be listed as icons that can be run sandboxed. Firetools and Firejail also support over 800 different applications so they too can be run after installing them. However, Snap and flatpak packages aren’t supported.
To run any of these, either right-click on them and choose Run or double-click them.
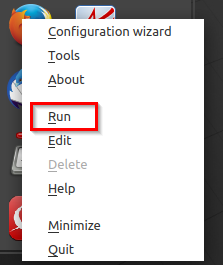
To see if the applications are running in the sandboxed mode, double-click on the Settings icon at the top from the Firetools menu or right-click and select Tools.
This will show a list of applications that are sandboxed along with their process IDs and the system resources that they are using.
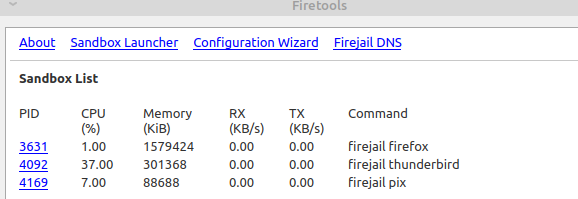
To know further details, click on their process IDs. It will show a graphical view of their usage. You can also shut down the applications from here by clicking on Shutdown.
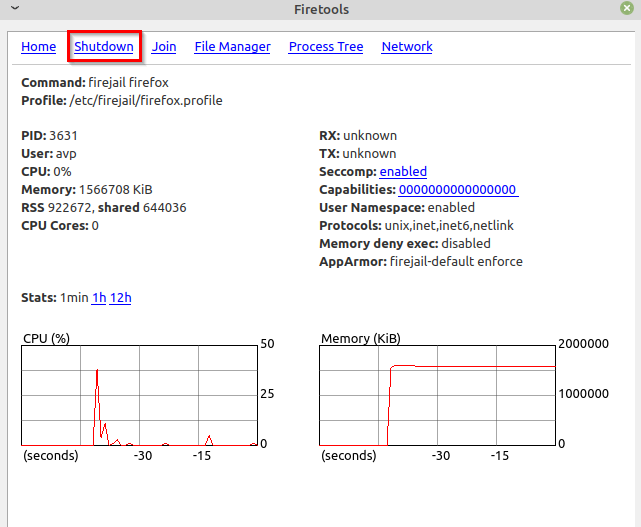
This will exit them from the sandboxed mode and also close them.
Creating custom sandboxes using Firetools:
Besides running the applications in the default sandbox, you can also create your own. This is useful when you need to add specific restrictions on a per-application basis.
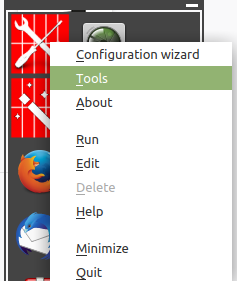
To configure a custom sandbox, click on the wizard icon from the Firetools menu, or right-click and select Configuration wizard.

Then select the application for custom sandboxing and choose Build a custom security profile. In this example, LibreOffice Writer is to be sandboxed so that all the documents created with it can only be saved to the Documents folder and not anywhere else.
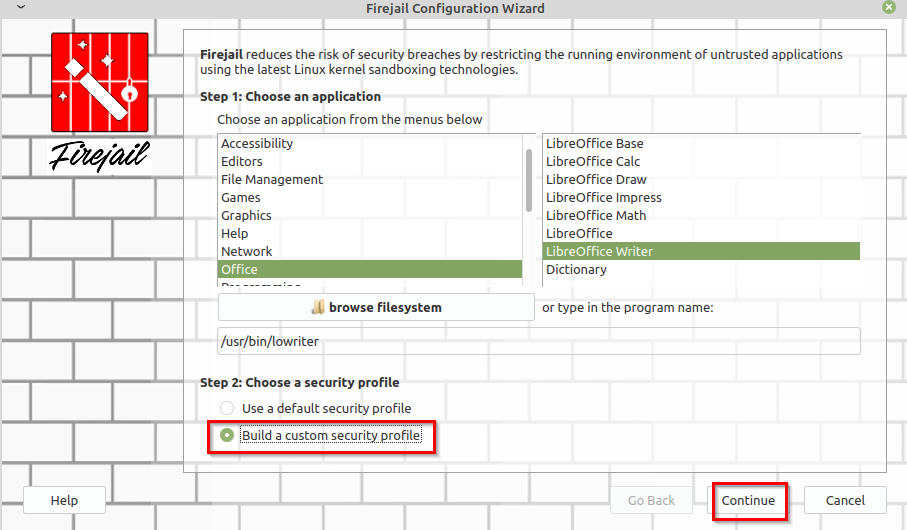
So, the option of Restrict /home directory is enabled for this (which is disabled by default). Then, all the other folders except Documents are unchecked which means that they can’t be accessed by LibreOffice Writer.
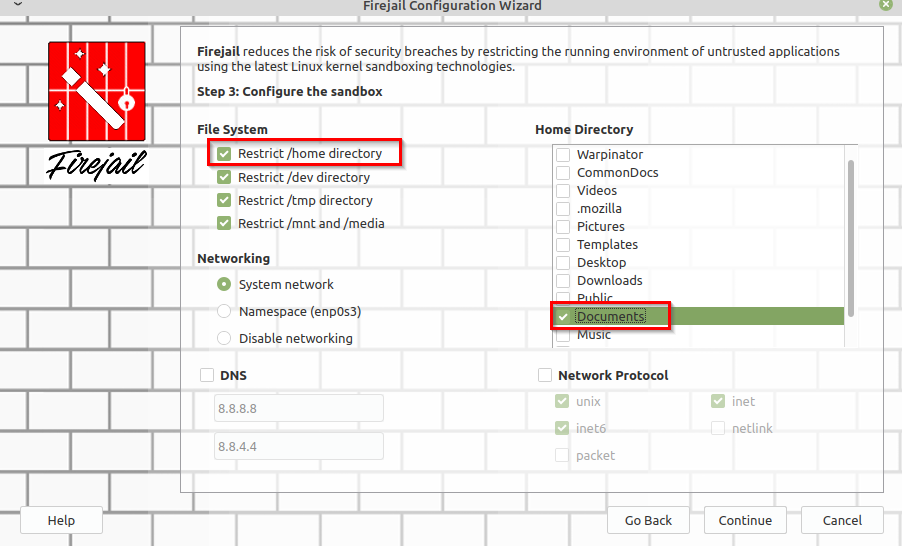
Click on Continue. In this example, other settings are left unchanged. You can however enable these for say sandboxing a browser or a multimedia program.
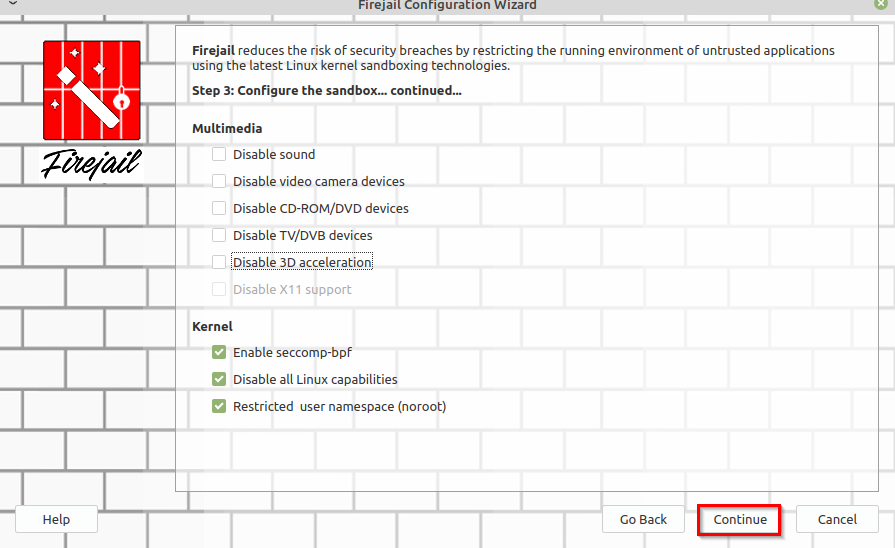
Click again on Continue. The sandbox monitoring and statistics option is disabled by default but can be enabled if needed. finally, finish by clicking on Done.
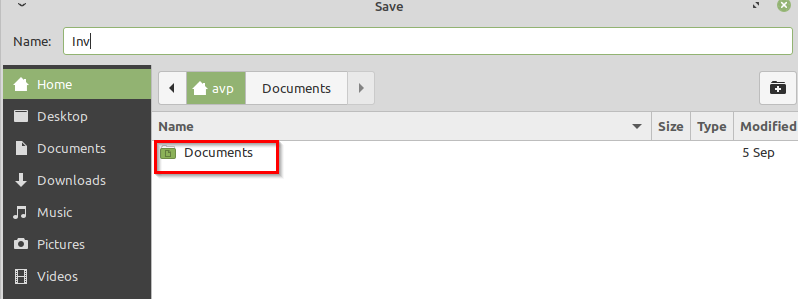
After this custom sandbox is created and when LibreOffice Writer is opened in it, no other folders except Documents can save the created files.
Similarly, you can make a custom sandbox for browsers and can restrict downloads to only a specific directory, prevent audio and video playback, and so on.
Using Firejail from the Linux command-line:
You can also directly use firejail from the command-line by typing in:
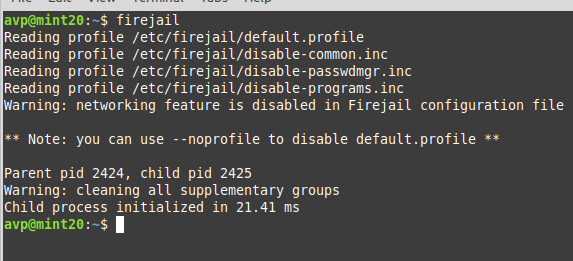
This will launch a jailed shell which will have certain restrictions. You can’t execute system-related tasks from this like rebooting, shutting down or switching to root, and so on.
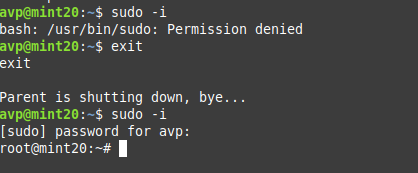
To do that, you’d need to first exit this jailed shell.
To run programs using firejail, use the command:
So, to open Firefox in the sandboxed mode, the command will be:
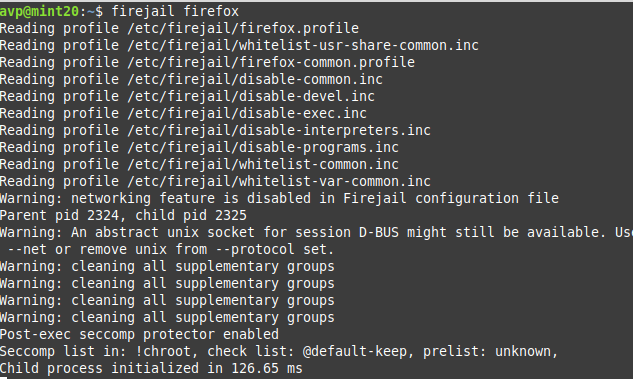
Similarly, to launch VLC player, the command will be:
You can also use other parameters like bandwidth, netstats, and so on. To know more, use the man command:
These apps that are started from the firejail command-line too can be managed with the Sandbox Launcher. However, using Firetools as a front-end makes it simpler to launch them, create custom sandboxes, and manage what is being sandboxed.
Happy sandboxing.